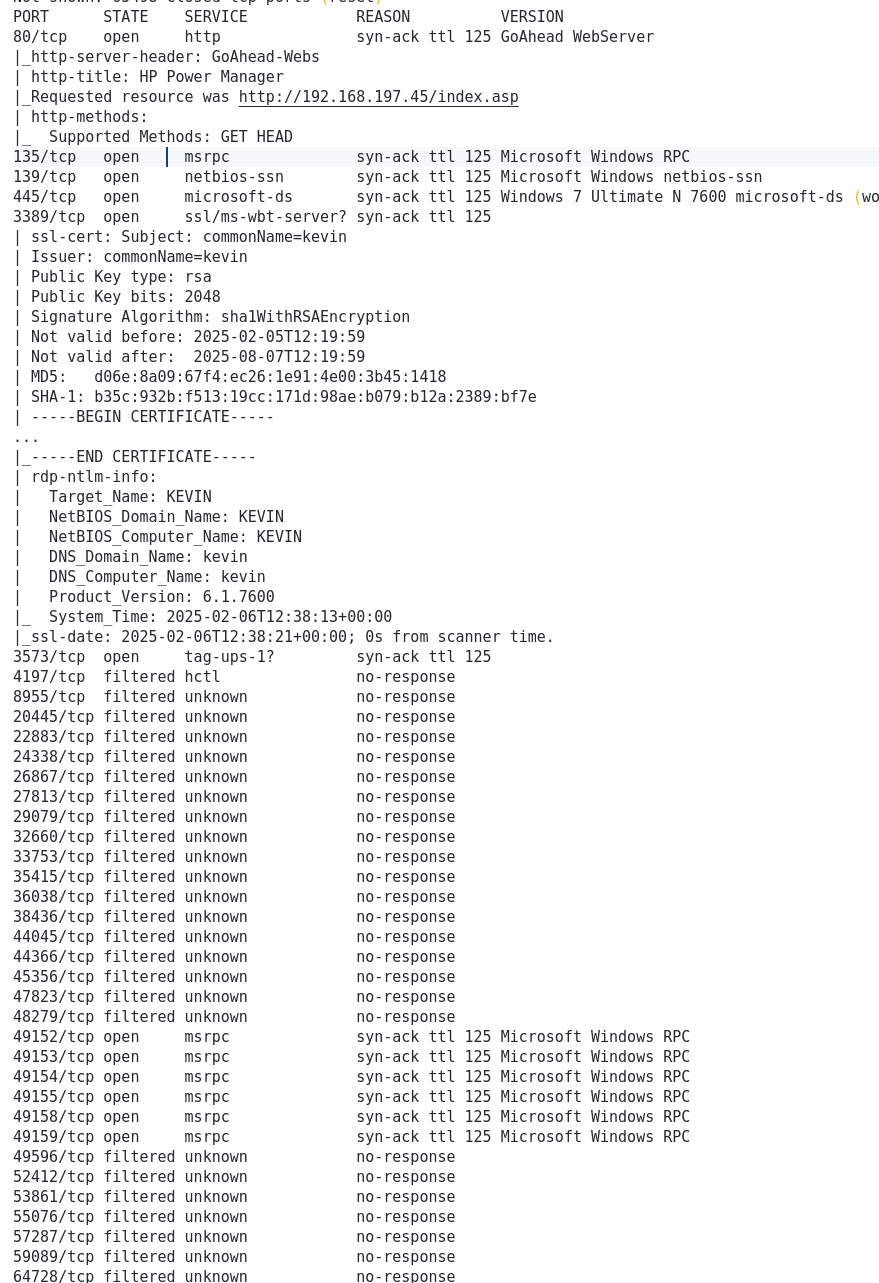
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
| - os
OS: Windows 7 Ultimate N 7600
OS version: '6.1'
OS release: ''
OS build: '7600'
Native OS: Windows 7 Ultimate N 7600
Native LAN manager: Windows 7 Ultimate N 6.1
- ports
- 80
HTTPServer[GoAhead-Webs]
HP Power Manager
Cyclade
+ /cgi-bin/dose.pl?daily&somefile.txt&|ls|: DailyDose 1.1 is vulnerable to a directory traversal attack in the 'list' parameter. See: OSVDB-2799
+ /cgi-bin-sdb/dose.pl?daily&somefile.txt&|ls|: DailyDose 1.1 is vulnerable to a directory traversal attack in the 'list' parameter. See: OSVDB-2799
+ /forum/memberlist.php?s=23c37cf1af5d2ad05f49361b0407ad9e&what=\">\"<script>javascript:alert(document.cookie)</script>: Vbulletin 2.2.9 and below are vulnerable to Cross Site Scripting (XSS). See: OSVDB-3280
+ /docs/<script>alert('Vulnerable');</script>: Nokia Electronic Documentation is vulnerable to Cross Site Scripting (XSS). See: http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2003-0801
- 139
[V] Trying to get NetBIOS names information, running command: nmblookup -s /tmp/tmpnxrjto4_ -A 192.168.197.45
[92m[+] Got domain/workgroup name: WORKGROUP[0m
[92m[+] Full NetBIOS names information:
- KEVIN <00> - B <ACTIVE> Workstation Service
- WORKGROUP <00> - <GROUP> B <ACTIVE> Domain/Workgroup Name
- WORKGROUP <1e> - <GROUP> B <ACTIVE> Browser Service Elections
- KEVIN <20> - B <ACTIVE> File Server Service
- WORKGROUP <1d> - B <ACTIVE> Master Browser
- ..__MSBROWSE__. <01> - <GROUP> B <ACTIVE> Master Browser
- MAC Address = 00-50-56-AB-F9-35[0m
- 445
[V] Trying to get NetBIOS names information, running command: nmblookup -s /tmp/tmpnxrjto4_ -A 192.168.197.45
SMB 1.0: true
SMB 2.02: true
SMB 2.1: true
smb-vuln-ms17-010:
| VULNERABLE:
| Remote Code Execution vulnerability in Microsoft SMBv1 servers (ms17-010)
| State: VULNERABLE
| IDs: CVE:CVE-2017-0143
| Risk factor: HIGH
| A critical remote code execution vulnerability exists in Microsoft SMBv1
| servers (ms17-010).
|
- 3389
ms-wbt-server
- 3573
tag-ups-1
- udp 137
netbios-ns
|